Law enforcement in eleven countries, including the Australian Federal Police, have taken over the infrastructure for the Flubot malware that started spreading worldwide in 2020-21.
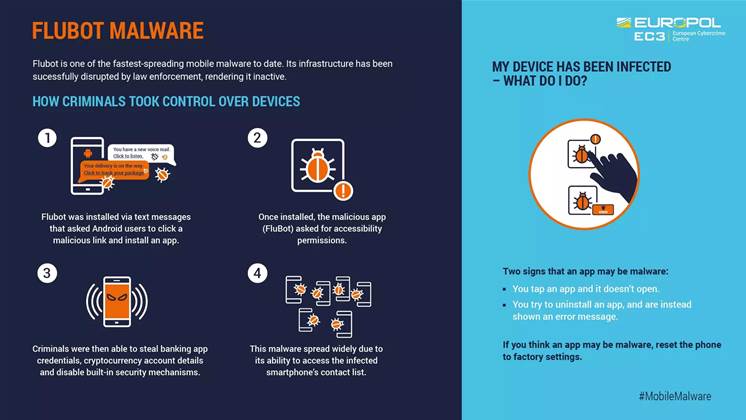
Flubot was spreading through malicious links in short messaging service (SMS) texts purporting to be package delivery or voice mail notifications sent to Android devices, an attack known as smishing.
Clicking on the malicious link caused the Flubot malware to be installed on users' phones.
The malware would request access permissions from users on their Android devices which if they were granted gave hackers a free run to capture banking app credentials and crypto currency accounts, and also disabled built-in security details, Europol said.
As Flubot captured users' contacts on the infected phones, "this strain of malware was able to spread like wildfire," Europol noted.
Dutch police were able to render Flubot inactive in May by taking over the malware's infrastructure.
Police forces in other European countries, Australia, and the United States cooperated in a worldwide investigation into Flubot, under the auspices of Europol's European Cybercrime Centre or EC3.
As of yet, the identity of the Flubot operators is not known.


























