A GPS vehicle tracker used by “militaries, law enforcement agencies, and corporations” as well as consumers has vulnerabilities serious enough to attract the attention of America’s Cybersecurity and Infrastructure Security Agency.

According to BitSight, which reported the bugs to CISA, the MiCODUS MV720 GPS vehicle tracker has users in 169 countries including Australia and New Zealand.
Its features include real-time monitoring of location and speed, historical routes taken by the vehicle, and the ability to cut off fuel in the event of theft.
Users can send commands to deployed devices over SMS or using an app.
CISA’s advisory warns of five vulnerabilities in particular:
- CVE-2022-2107 – A hard-coded master password in the device’s server, which mean an attacker can issue commands to the tracker as if they came from the owner;
- CVE-2022-2141 – SMS commands can be issued without authentication;
- CVE-2022-2199 – A cross-site scripting bug in the system’s main web server;
- CVE-2022-34150 and CVE-2022-33944 – Authentication bypasses in the web server.
“As of July 18th, 2022, MiCODUS has not provided updates or patches to mitigate these vulnerabilities”, CISA noted.
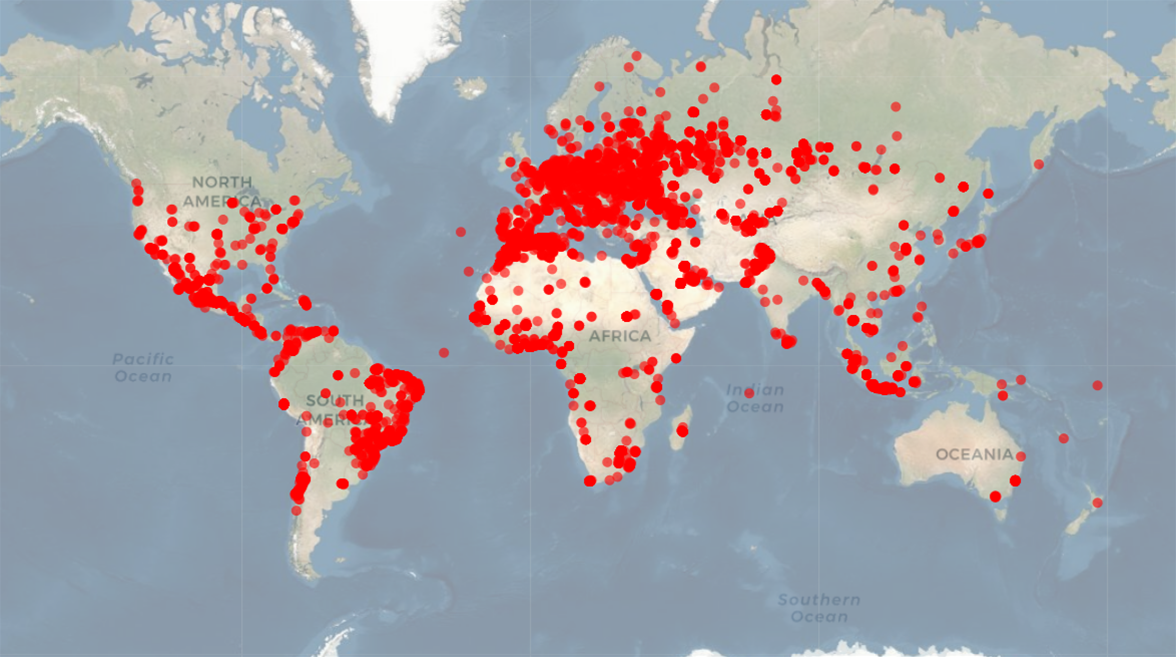
The upshot of all this, BitSight wrote, is that attackers “could potentially cut off fuel, physically stop vehicles, or surveil movement of vehicles in which the device is installed.”
Since the vulnerabilities give an attacker access to communications between to and from the tracker, potential attacks include “intentionally issuing incorrect vehicle location information to the GPS server”.


























