Microsoft has set up an early access program for secure enclaves in its Azure cloud computing platform that fully encrypt and protect data in use to render it inaccessible to anyone not the owner.
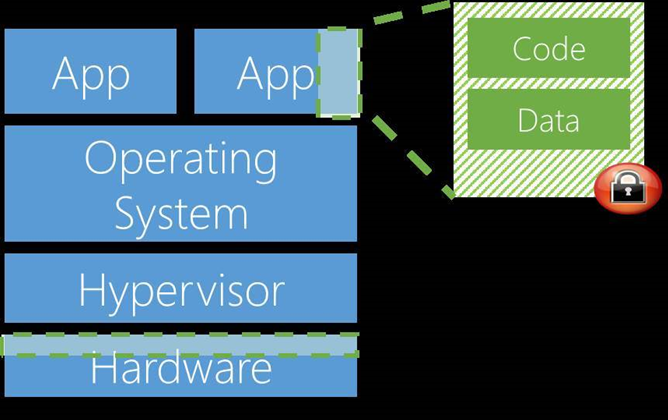
Known as Azure confidential computing, the offering will keep data and code within trusted execution environments (TEEs) that prevent anyone viewing or tampering it from the outside, even with debugging software.
Only authorised users and code can access the data within TEEs. If the code is tampered with, the operations are denied and the TEE is disabled, Microsoft said.
This means not even Microsoft can access data protected by TEEs in Azure, and could not be compelled by governments to hand over information.
The TEEs will protect against threats such as insiders with administrative privileges, or direct access to the hardware that the data is stored or processed on.
Hacking and malware attacks via operating system, application and hypervisor exploits are likewise foiled by the use of TEEs, Microsoft said.
A software and a hardware TEE will be supported by Azure confidential computing. This includes the company's software-based virtual secure mode (VSM) in the Windows 10 and Windows Server 2016 Hyper-V hypervisor.
When VSM is enabled for applications, sensitive code and data can be isolated in its own protected virtual machine.
VSM provides a minimal operating system image with memory that is kept seperate and protected from the main virtual machine that applications run under, using processor virtualisation extensions.
Customers who don't want a Microsoft TEE can use the hardware-based Intel software guard extensions (SGX) - which are found in the seventh generation Core and Xeon E3 version 5 processors - on specific servers in Azure.
Microsoft envisages the secure enclave-based confidential computing offering to appeal to financial service and healthcare providers, as well as organisations that need strong protection for their intellectual property while it is used in the cloud.

























