The unknown attackers that breached communications company Twilio tried to hack reverse proxy provider Cloudflare using similar social engineering techniques, but were thwarted.
Cloudflare said its use of hardware keys for authentication, and the company's Zero Trust security solution, protected its network.
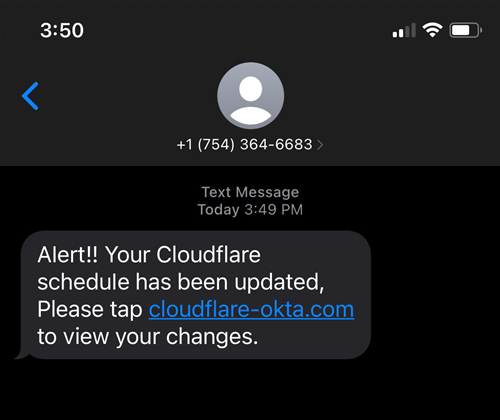
In a post-mortem of the attack, Cloudflare founder Matthew Prince and engineers Daniel Stinson-Diess and Sourov Zaman wrote that on July 20, at least 76 employees, including some of their family members, were sent legitimate looking text messages.
The messages contained a link to a purported Cloudflare Okta login page, and as in the case of Twilio, asked employees to check schedule changes.
Okta is Cloudflare's identity provider.
Cloudflare said the messages were sent from four phone numbers on United States telco T-Mobile's network, and the phishing domain in question had been registered less than 40 minutes before the attack started.
The company monitors when domains that use the Cloudflare brand name are registered; however, the phishing site was registered and published as a .com domain so close to the attack that the company's systems didn't detect it.
As with the Twilio attack, the phishing domains were registered with Porkbun.
Attackers received captured credentials via Telegram, and the phishing system was also set up to relay time-based one time passwords (TOTP) that employees entered on the site.
This, Cloudlare said, would be sufficient to defeat most two-factor authentication (2FA) implementations.
A remote access software, AnyDesk, was also downloaded by the phishing site, which if installed would've given the attackers full control over victims' machines.
In all, three employees fell for the phishing scam but as Cloudflare uses hardware keys like Yubico's Yubikey, which authenticate users locally, the attackers could not login and access the company's internal systems.
The three were not reprimanded, Cloudflare said.
"We’re all human and we make mistakes.
"It’s critically important that when we do, we report them and don’t cover them up," the company said.
Cloudflare notes that it has not experienced any successfull phishing attacks since it rolled out hardware keys.
Blocking the malicious domains was also done, with the three compromised employees had their credentials reset and active sessions closed.
At this stage, it is not known who the attackers are, or how they were able to collate employee phone numbers, but Cloudflare said it found no indication that its directory services had been breached.
Working with hosting provider DigitalOcean, on which the attackers ran the phishing site, Cloudflare were able to glean some details, such as a US-based dedicated service provider was used in the phishing campaign, with hosts in Toronto, Canada, and Washington DC.
The attacks appear to be part of a larger campaign, as Twilio said it has heard of other providers being targeted.
Cloudflare also believes the attacker is targeting multiple organisations, and that the attack is sophisticated enough that most of them are likely to be breached.

























